Hatchet
About Hatchet
Hatchet serves as an AI Copilot for incident response, targeting on-call engineers dealing with tier-1 services. It enhances workflows by quickly triaging and investigating incidents, suggesting fixes based on logs and code analysis, ultimately resolving issues faster and reducing downtime for critical services.
Hatchet offers flexible pricing plans tailored for companies scaling from Series B to D. Each tier provides distinct features aimed at optimizing incident response. Users can benefit from upgrades, gaining access to advanced analytics and support, making it a valuable investment for critical service management.
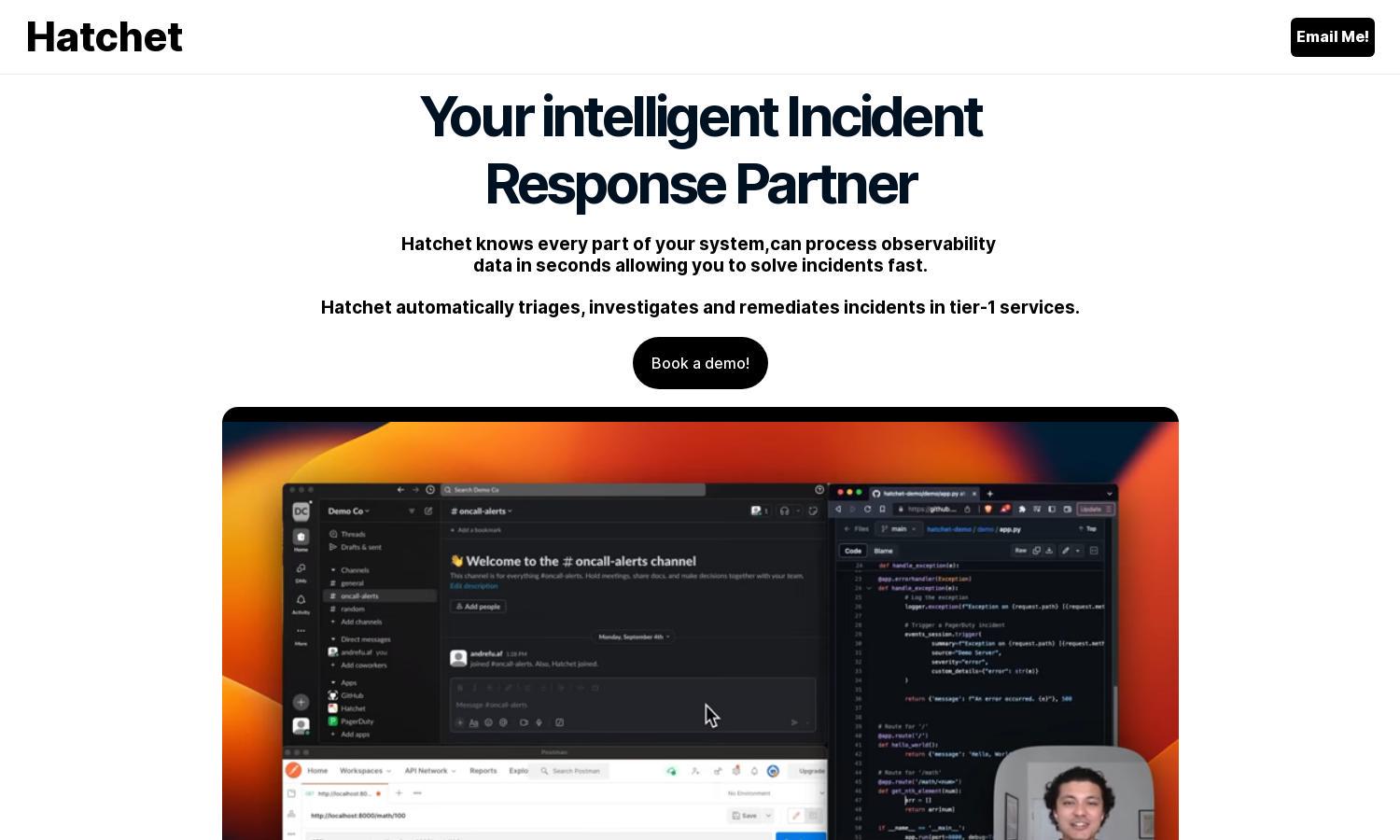
The user interface of Hatchet is designed for seamless navigation, featuring a clean layout that prioritizes ease of use. Users can quickly access logs and initiate investigations, enhancing productivity. Unique interactive elements ensure users can maximize Hatchet's capabilities effortlessly while managing incident responses efficiently.
How Hatchet works
To start with Hatchet, users onboard by integrating it into their alerting system, pointing it to relevant log files. The platform then reads logs and analyzes communication channels, suggesting actionable fixes during incidents. Users can easily navigate its features to resolve issues swiftly, enhancing their incident management process.
Key Features for Hatchet
AI-Driven Triage
Hatchet's AI-driven triage simplifies incident management, enabling users to quickly analyze logs and identify issues. This dynamic feature enhances productivity, allowing on-call engineers to resolve pages faster and more effectively, resulting in less downtime and increased operational efficiency.
Seamless Integration
Hatchet offers seamless integration with existing alerting systems, allowing users to implement it effortlessly. By simply pointing Hatchet to service logs, users can leverage its capabilities to streamline incident responses, ultimately improving their workflow and service reliability.
Complete Data Security
Hatchet ensures complete data security through self-hosted deployments, with zero telemetry involved. This unique feature allows organizations to control their data while utilizing AI for incident response, addressing security concerns and making it suitable for sensitive environments.