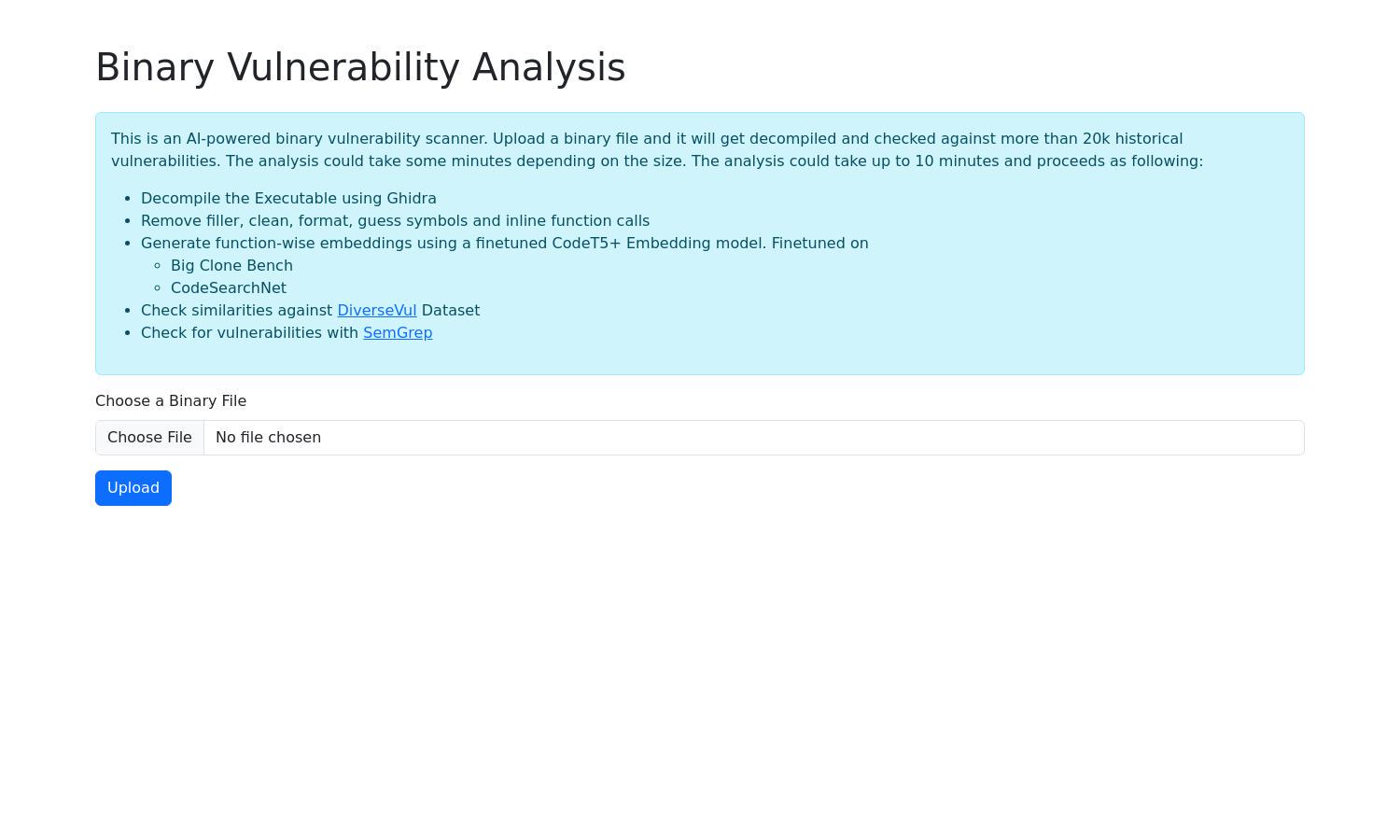
Binary Vulnerability Analysis
About Binary Vulnerability Analysis
Binary Vulnerability Analysis is an advanced AI-driven tool designed to enhance software security by scanning binary files for vulnerabilities. By leveraging cutting-edge algorithms, it decompiles executables and checks them against extensive historical data, providing developers with insights to mitigate risks effectively and improve resilience.
Binary Vulnerability Analysis is currently free for users, with plans for premium tiers offering enhanced features and more extensive vulnerability databases in the future. Early users may benefit from exclusive discounts as the platform expands, ensuring comprehensive protection against emerging threats and vulnerabilities in software applications.
The user interface of Binary Vulnerability Analysis is designed for simplicity and efficiency, fostering a seamless browsing experience. Its intuitive layout guides users through uploading binaries, viewing analyses, and exploring vulnerabilities, making it accessible for all skill levels while promoting effective security assessments.
How Binary Vulnerability Analysis works
To use Binary Vulnerability Analysis, users start by uploading a binary file to the platform. The site then employs Ghidra for decompilation, streamlining the code for analysis. The tool generates contextual embeddings and checks against a vast dataset of vulnerabilities, delivering a comprehensive report on potential security risks in an intuitive, user-friendly manner.
Key Features for Binary Vulnerability Analysis
AI-Powered Vulnerability Detection
Binary Vulnerability Analysis uniquely utilizes AI to detect vulnerabilities by analyzing binary files against a database of over 20k historical vulnerabilities, allowing developers to enhance their security posture and address critical issues before they can be exploited, ultimately protecting their applications.
Decompilation and Code Analysis
One standout feature of Binary Vulnerability Analysis is its decompilation capability using Ghidra, which cleans and formats binary code effectively. This process allows users to gain insights into executable files, revealing potential vulnerabilities and ensuring that developers can make informed adjustments to enhance security.
Function-Wise Embeddings Generation
Binary Vulnerability Analysis generates function-wise embeddings using a fine-tuned CodeT5+ Embedding model. This innovative feature aids in precise detection of vulnerabilities, enabling users to better understand their code structure and enhance their ability to mitigate risks associated with potential vulnerabilities in their software.